VPN Stealth Mode: Fly Under the Radar with These Tricks
Are you looking for a way to browse the internet anonymously and securely? With VPN stealth mode, you can fly under the radar and protect your privacy while browsing the web. This article will provide an overview of what stealth mode is, the benefits of using it, and tips for setting it up. With these steps, you’ll be able to enjoy secure online activities without worry.
Key Takeaways:
The VPN stealth mode option is a great choice for those looking to protect their online privacy and security. This technology is designed to disguise your real IP address, making it difficult for websites, hackers, and other third parties to track your activities online. With VPN stealth mode turned on, it’s possible to browse the web anonymously and securely without worrying about who may be watching.
Not all VPNs offer stealth mode, so it’s important to do your research and find one that does. When you’re looking for a VPN that supports stealth mode, make sure to read reviews and compare features. You’ll also want to consider the speed of the connection, as well as if the service allows for unlimited data usage.
What is a ‘Stealth’ VPN?
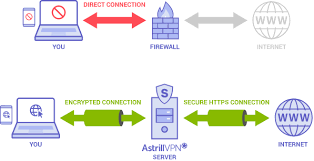
VPN Stealth Mode
A ‘Stealth’ VPN, also known as an obfuscated VPN or stealth mode, is a special feature offered by some VPN providers that allows users to fly under the radar and bypass strict online restrictions. It essentially disguises VPN traffic as regular internet traffic, making it harder for governments, ISPs, and other surveillance entities to detect and block VPN usage.
But how does a ‘Stealth’ VPN work? Well, when you connect to a regular VPN server, your data is encrypted and tunneled through the VPN server, which can still be detected by deep packet inspection (DPI) systems. However, with a ‘Stealth’ VPN, additional encryption and obfuscation techniques are applied to the VPN traffic, making it appear as regular HTTP or HTTPS traffic.
This stealthy feature is especially useful in countries that heavily censor or restrict internet access, such as China, Iran, or Russia. These countries employ sophisticated DPI systems that can detect and block VPN connections. By using a ‘Stealth’ VPN, users can bypass these restrictions and access the open internet without their online activities being monitored or tracked.
Moreover, a ‘Stealth’ VPN not only helps users access blocked content and maintain their online privacy but also enhances their overall security. The additional layer of encryption and obfuscation provided by a ‘Stealth’ VPN ensures that no one can see or intercept your data, keeping your online activity truly private and secure.
To employ a ‘Stealth’ VPN, all you need is a reputable VPN provider that offers this feature. Many top VPN services, such as Private Internet Access, offer ‘Stealth’ or obfuscated servers as part of their security toolkit. These servers are strategically located in countries with more relaxed internet restrictions, enabling users to bypass censorship and access the content they desire.
In conclusion, a ‘Stealth’ VPN is a powerful tool for those seeking to maintain their online privacy, bypass geographical restrictions, and add an extra layer of security to their internet connection. By disguising VPN traffic as regular internet traffic, users can evade censorship, surveillance, and enjoy a truly open and secure online experience. So, if you value your online freedom and want to fly under the radar, consider utilizing the power of a ‘Stealth’ VPN.
Why use obfuscation?
Obfuscation is a powerful tool that can greatly enhance your online security and privacy. In today’s digital age, where online surveillance and censorship are on the rise, it has become crucial to protect your sensitive information and maintain your freedom on the internet. That’s where obfuscation comes in.
Obfuscation is the process of disguising or hiding information, in this case, your VPN traffic, to make it difficult for anyone to detect or understand. By using obfuscation techniques, you can bypass various network restrictions, including firewalls, deep packet inspection (DPI) systems, and VPN blocks.
So, why should you use obfuscation? Well, there are several compelling reasons:
1. Bypassing censorship: Obfuscation allows you to bypass internet censorship imposed by governments, ISPs, or other entities. In countries like China, Iran, or Russia, where internet restrictions are prevalent, obfuscation can help you access the open internet without being detected or blocked.
2. Evading deep packet inspection: DPI systems are capable of analyzing and categorizing internet traffic, including VPN traffic. By obfuscating your VPN traffic, you can make it indistinguishable from regular HTTP or HTTPS traffic, preventing DPI systems from identifying and blocking your VPN connection.
3. Protecting privacy: Obfuscation adds another layer of privacy to your online activities. By making your VPN traffic look like regular encrypted web traffic, obfuscation helps conceal your online activities from prying eyes, including government surveillance agencies, ISPs, and hackers.
4. Enhancing security: Obfuscation strengthens the security of your VPN connection by making it harder for attackers to target or intercept your data. The additional encryption and obfuscation provided by obfuscated servers or stealth VPNs ensure that your data remains secure and immune to potential attacks.
5. Accessing blocked content: Obfuscation can help you access geo-restricted or blocked content on popular streaming services, bypassing their VPN blocks or detection mechanisms. It enables you to enjoy your favorite shows, movies, or sports events, regardless of your location.
In conclusion, obfuscation is a vital tool for anyone concerned about their online security, privacy, and unrestricted access to the internet. By utilizing obfuscation techniques through a reputable VPN provider, you can fly under the radar, bypass censorship, protect your privacy, and stay secure in the digital world. So, consider incorporating obfuscation into your VPN toolkit and enjoy a truly open and private online experience.
How a ‘Stealth’ VPN works
A ‘Stealth’ VPN, also known as an obfuscated VPN, is a powerful tool that allows you to fly under the radar and bypass various network restrictions. But how exactly does it work?
At its core, a ‘Stealth’ VPN employs obfuscation techniques to make your VPN traffic appear like regular encrypted web traffic. By doing so, it becomes incredibly difficult for anyone to detect or block your VPN connection. This is achieved by disguising the VPN traffic to resemble HTTPS or HTTP traffic, which is typically allowed on most networks.
When you connect to a ‘Stealth’ VPN server, your data is first encrypted using robust AES 256-bit encryption. This encryption ensures that your data remains secure and protected from potential attackers. However, the encryption alone doesn’t make it ‘stealthy.’
To achieve obfuscation, the ‘Stealth’ VPN adds another layer of complexity to your traffic by disguising it. It alters the packet headers, masks the VPN protocol, and even hides the fact that you are using a VPN. This makes it incredibly challenging for network monitoring systems, deep packet inspection (DPI) systems, and VPN blocks to identify or block your connection.
By making your VPN traffic appear like regular web traffic, a ‘Stealth’ VPN enables you to bypass various forms of censorship. In countries that impose strict internet restrictions, like China or Iran, this can be a game-changer. You can access the open internet, social media platforms, and even blocked websites without being detected or blocked.
Moreover, a ‘Stealth’ VPN adds an extra layer of privacy to your online activities. By obfuscating your VPN traffic, it helps prevent prying eyes, including government surveillance agencies, ISPs, and hackers, from monitoring or tracking your online activities. This ensures that your privacy is maintained and your sensitive data remains secure.
Additionally, a ‘Stealth’ VPN enhances the overall security of your VPN connection. By making it harder for attackers to target or intercept your data, it adds a crucial layer of protection. With the added encryption and obfuscation, your data remains safe from potential threats, ensuring that your online experience is secure and worry-free.
Furthermore, a ‘Stealth’ VPN can help you access geo-restricted or blocked content on popular streaming services. By bypassing VPN detection mechanisms implemented by these services, you can enjoy your favorite shows, movies, or sports events, regardless of your location.
In conclusion, a ‘Stealth’ VPN is an excellent tool for those who value online privacy, security, and freedom. By employing obfuscation techniques, it enables you to bypass censorship, evade deep packet inspection, protect your privacy, enhance security, and access blocked content. With a ‘Stealth’ VPN, you can fly under the radar and enjoy a truly unrestricted and private online experience.
What’s HTTPS?
HTTPS stands for Hypertext Transfer Protocol Secure, and it is the secure version of HTTP, the protocol used for transmitting data over the internet. While HTTP transfers data in plain text, making it vulnerable to interception and tampering, HTTPS adds an extra layer of security by encrypting the data.
One of the key components of HTTPS is SSL/TLS, which stands for Secure Sockets Layer/Transport Layer Security. SSL/TLS uses cryptographic algorithms to encrypt data that is being transmitted between a web browser and a website. This encryption ensures that sensitive information, such as passwords, credit card details, and personal data, is protected from being intercepted by malicious third parties.
To establish a secure connection, a website needs to obtain an SSL/TLS certificate from a trusted certificate authority (CA). This certificate verifies the authenticity of the website’s identity and encrypts the data exchanged between the server and the user’s browser.
When a user visits a website that uses HTTPS, their browser verifies the website’s SSL/TLS certificate. If the certificate is valid and trustworthy, a secure connection is established. This is indicated by a padlock icon in the browser’s address bar and the URL starting with “https://” instead of “http://”. These visual cues provide users with the assurance that their communication with the website is secure.
HTTPS offers several advantages over HTTP. Firstly, it protects the confidentiality of data by encrypting it, making it difficult for unauthorized individuals to access or decipher. Secondly, it ensures the integrity of data by detecting any alterations or tampering during transmission. If any modifications are detected, the connection is terminated to prevent the user from unknowingly interacting with a compromised website. Lastly, HTTPS provides authentication, allowing users to trust that they are communicating with the intended website and not an impostor.
In recent years, there has been a significant push towards making the entire web more secure, with major browsers and search engines encouraging websites to adopt HTTPS. This increased emphasis on security is driven by the need to protect users’ privacy and sensitive information in an increasingly interconnected and data-driven world.
In conclusion, HTTPS is a vital component of internet security, offering protection against eavesdropping, data tampering, and identity impersonation. By encrypting data and verifying the authenticity of websites, HTTPS ensures that users can browse the web with confidence, knowing that their sensitive information is secure.
How your data is converted to ‘stealth’ packets
In the world of online privacy and security, the term “stealth” often comes up when discussing VPNs and their ability to fly under the radar of prying eyes. But have you ever wondered how exactly your data is converted into these elusive “stealth” packets? Let’s take a closer look.
When you connect to a VPN, your data is first encrypted using robust encryption algorithms, such as AES 256-bit encryption. This encryption ensures that your data is virtually impossible to decipher, even if intercepted by cybercriminals or government surveillance agencies. However, encryption alone does not make your data stealthy; it merely makes it secure.
To achieve the stealth factor, VPN providers employ a technique called packet obfuscation. This process involves disguising your encrypted data as regular traffic, making it indistinguishable from any other internet activity. The aim is to make it difficult for anyone monitoring your internet connection to identify that you are using a VPN.
How does this packet obfuscation work in practice? Well, VPN providers typically assign specific ports to various types of internet traffic. For example, HTTP web browsing traffic might use port 80, while email traffic might use port 25. These conventional ports are easily identifiable by network monitoring tools, raising suspicion that a VPN may be in use.
To combat this, VPNs use a technique called “port masking” or “port hopping” to prevent your encrypted data packets from being associated with specific ports. Instead of using the standard port numbers, the VPN will assign random or non-standard ports to your data packets. By doing so, your VPN traffic blends in with regular internet traffic, making it harder to detect and block.
Additionally, some VPNs may also incorporate a feature known as “Deep Packet Inspection (DPI) evasion.” DPI is a technique used by internet service providers and other network administrators to analyze and control internet traffic. By employing DPI evasion techniques, VPNs can circumvent these inspections, further enhancing the stealthiness of your data packets.
It’s important to note that not all VPNs offer the same level of packet obfuscation. If stealthiness is a crucial factor for you, make sure to choose a VPN that specifically advertises obfuscated servers or stealth mode. These VPNs have implemented advanced techniques to ensure that your data remains hidden from prying eyes.
In conclusion, the process of converting your data into “stealth” packets involves encrypting it with robust encryption algorithms and then using packet obfuscation techniques to disguise the encrypted data as regular internet traffic. By doing so, VPNs add an extra layer of security and privacy, making it incredibly difficult for anyone to monitor or intercept your online activities. So, if you’re concerned about your online privacy and want to fly under the radar, consider using a VPN with stealth capabilities to ensure your data remains hidden and protected.
Step #1 – Start with regular OpenVPN encrypted data
When it comes to achieving VPN stealth mode, the first step is to start with regular OpenVPN encrypted data. OpenVPN is a popular open-source VPN protocol that provides a secure and reliable connection. By encrypting your data with OpenVPN, you ensure that your information is protected from any unauthorized access.
To start with regular OpenVPN encrypted data, you need to choose a VPN service that supports OpenVPN. Many reputable VPN providers offer OpenVPN as one of their protocol options. Once you have subscribed to a VPN service, you can download and install their VPN client on your device.
After installing the VPN client, you can launch the application and log in with your credentials. Most VPN clients have a user-friendly interface that allows you to easily connect to a server of your choice. You can typically select a server based on location or other factors, such as server load or specialty servers for streaming or torrenting.
Once you have established a connection to a VPN server, your data will be encrypted using the OpenVPN protocol. This encryption ensures that any information transmitted through your internet connection is secure and not easily readable by hackers or surveillance agencies.
By using regular OpenVPN encrypted data as the foundation of your VPN connection, you lay the groundwork for a secure and private online experience. However, it is important to note that while OpenVPN encryption provides a strong level of security, it may not be enough to achieve complete stealthiness.
To enhance the stealth factor of your VPN connection, additional techniques such as packet obfuscation and deep packet inspection evasion may be necessary. These techniques disguise your VPN traffic as regular internet activity, making it harder for anyone monitoring your connection to detect and block your VPN usage.
In conclusion, starting with regular OpenVPN encrypted data is the first step towards achieving VPN stealth mode. It provides a solid foundation for securing your online activities and protecting your data from prying eyes. However, to truly fly under the radar and maximize your privacy, you may need to implement further measures such as packet obfuscation and deep packet inspection evasion.
Obfsproxy
One effective technique to achieve stealthiness with your VPN connection is through the use of obfsproxy. Obfsproxy, short for “obfuscated proxy,” is a tool that helps disguise your VPN traffic and makes it difficult for network administrators or ISPs to detect and block your VPN usage.
Obfsproxy works by adding an extra layer of obfuscation to your VPN traffic, making it appear as regular internet traffic. It does this by modifying the packet headers and payload of your VPN data, making it indistinguishable from other types of internet traffic.
When you enable obfsproxy on your VPN client, it will scramble your VPN traffic in a way that network filters or firewalls cannot easily identify it as VPN traffic. Instead, it will resemble normal HTTP (Hypertext Transfer Protocol) traffic or other common protocols.
This obfuscation technique is especially useful in countries or regions where VPN usage is restricted or actively monitored. By disguising your VPN connection as regular web browsing or file downloading, you can bypass censorship measures and enjoy a more private and secure online experience.
Obfsproxy is especially effective when used in conjunction with other privacy-enhancing techniques, such as encrypted DNS (Domain Name System) resolution and a strict no-logs policy. By combining these techniques, you can create a highly stealthy and secure VPN connection that helps protect your online activity from prying eyes.
It is worth noting that not all VPN providers support obfsproxy. However, there are several reputable VPN services that offer this feature as part of their security toolkit. Before subscribing to a VPN service, make sure to check if they offer obfsproxy or any other obfuscation techniques.
In conclusion, obfsproxy is a valuable tool to further enhance the stealthiness of your VPN connection. By disguising your VPN traffic as regular internet activity, you can bypass restrictions, evade surveillance, and maintain your online privacy. When combined with other privacy-enhancing features, obfsproxy adds an extra layer of security and peace of mind to your VPN experience.
Pros
Pros of using VPN stealth mode
Using VPN stealth mode can provide several benefits for users seeking enhanced online privacy and security. Here are some of the key advantages of utilizing obfsproxy or other obfuscation techniques:
1. Evade censorship and restrictions: In countries or regions where internet censorship is prevalent, VPN stealth mode can be a game-changer. By disguising your VPN traffic as regular internet traffic, you can bypass censorship measures and access blocked websites, social media platforms, or messaging apps. This is particularly crucial for individuals who rely on unrestricted access to information or need to communicate freely.
2. Enhanced privacy: VPN stealth mode adds an extra layer of privacy to your online activities. By obfuscating your VPN traffic, it becomes more challenging for third parties, such as internet service providers, government agencies, or hackers, to monitor or track your online behavior. This is especially significant for protecting sensitive information, such as personal data, financial transactions, or confidential communications.
3. Improved security: VPN stealth mode offers an additional level of security to safeguard your internet connection. By concealing your VPN usage, obfuscation makes it harder for potential attackers or malicious entities to detect and target your VPN traffic. This can reduce the risk of cyber threats, including man-in-the-middle attacks, session hijacking, or data interception.
4. Bypass VPN blocking: Some networks or organizations may actively block or restrict access to VPN connections. By using VPN stealth mode, you can circumvent these restrictions and continue using your VPN service even in highly restrictive environments. This ensures that you can maintain a secure and private internet connection even when faced with VPN blocking measures.
5. Compatible with multiple devices and platforms: Many VPN providers offer obfsproxy or other obfuscation techniques across various devices and operating systems. This means you can enjoy VPN stealth mode not only on your computer but also on mobile devices, such as smartphones or tablets. This versatility allows you to protect your online activities across different platforms while maintaining a high level of privacy and security.
In conclusion, VPN stealth mode, enabled through obfsproxy or other obfuscation techniques, can significantly enhance your online privacy and security. By disguising your VPN traffic as regular internet activity, you can bypass censorship, protect sensitive information, and maintain a secure connection, even in restrictive environments. When selecting a VPN service, make sure to choose one that supports obfuscation features to take advantage of these benefits.
ShadowSOCKS
ShadowSOCKS is a popular protocol that is often used in conjunction with VPNs to provide enhanced privacy and security. Developed in China as a way to bypass the Great Firewall, ShadowSOCKS has gained a reputation for its ability to fly under the radar and evade VPN blocking measures. In this article, we will explore what ShadowSOCKS is, how it works, and why it is a fantastic option for users seeking an extra layer of security.
ShadowSOCKS is an open-source proxy protocol that helps users bypass internet censorship and access blocked content. Unlike traditional VPN protocols that encrypt all traffic, ShadowSOCKS focuses on only encrypting specific internet traffic. This makes it more difficult for firewalls and network administrators to detect and block VPN connections, as ShadowSOCKS traffic appears more similar to regular internet traffic.
The key feature of ShadowSOCKS is its ability to disguise VPN traffic as HTTPS traffic. By utilizing a technique called “socks5,” ShadowSOCKS socksifies the VPN traffic, making it look like regular encrypted web traffic. This helps users bypass firewalls and access blocked websites or online services that would otherwise be restricted.
One of the primary advantages of using ShadowSOCKS is its ability to provide faster speeds compared to traditional VPN protocols. As ShadowSOCKS only encrypts specific traffic, it reduces the processing overhead and can result in faster and more consistent speeds. This makes it an excellent option for activities that require high bandwidth, such as streaming or gaming.
In addition to speed, ShadowSOCKS also provides robust encryption to protect user data and ensure online privacy. It utilizes industry-standard encryption algorithms, such as AES 256-bit encryption, to secure the data transmission between the client and the server. This level of encryption ensures that your online activities and personal information remain private and secure.
Another advantage of ShadowSOCKS is its compatibility with various devices and platforms. Many VPN providers offer ShadowSOCKS as an option, allowing you to use it on different operating systems, including Windows, macOS, iOS, and Android. This versatility enables you to enjoy the benefits of ShadowSOCKS on your computer, smartphone, or tablet, ensuring that your online activities are protected across multiple devices.
Furthermore, ShadowSOCKS also provides an extra layer of security by preventing deep packet inspection (DPI). DPI is a technique used by network administrators to analyze and filter internet traffic based on its content. With ShadowSOCKS, your VPN traffic is disguised as regular encrypted web traffic, making it more challenging for DPI systems to detect and block the connection. This ensures that your internet activities remain private and secure, even in highly restrictive environments.
In conclusion, ShadowSOCKS is an excellent option for users seeking enhanced online privacy and security. Its ability to disguise VPN traffic as regular web traffic, provide faster speeds, and offer robust encryption make it a powerful tool for bypassing censorship, accessing blocked content, and protecting your online activities. Whether you’re in a country with heavy internet restrictions or simply want an extra layer of security, ShadowSOCKS is definitely worth considering.
SSTP
SSTP, or Secure Socket Tunneling Protocol, is another powerful tool in the realm of VPNs that offers users a reliable and secure method of bypassing internet censorship and ensuring online privacy. Developed by Microsoft, SSTP provides an impressive level of protection and encryption for your data transmission, making it an excellent choice for those seeking maximum security.
One of the standout features of SSTP is its ability to operate over the HTTPS protocol. By utilizing this widely accepted and encrypted web protocol, SSTP disguises VPN traffic as regular web traffic. This means that network administrators and firewalls are less likely to detect and block SSTP connections, allowing you to access restricted content and websites with ease.
In addition to its stealthy nature, SSTP also boasts robust encryption capabilities. It employs the industry-standard AES 256-bit encryption, ensuring that your data remains secure and protected. This advanced encryption algorithm is virtually unbreakable, providing users with peace of mind that their online activities are shielded from prying eyes.
SSTP is also known for its compatibility with various platforms and devices. It is supported on Windows operating systems as it was developed by Microsoft. However, many VPN providers also offer SSTP as an option for other platforms, including macOS, iOS, and Android. This flexibility allows you to enjoy the benefits of SSTP across multiple devices, ensuring that your online activities remain private and secure, regardless of the operating system you use.
Another advantage of SSTP is its ability to bypass network restrictions without sacrificing connection speeds. Unlike some VPN protocols that may lead to slower speeds due to the encryption and decryption processes, SSTP offers reliable and faster connections. This makes it an ideal choice for activities that require high bandwidth, such as streaming movies, gaming, or downloading large files.
Furthermore, SSTP provides an extra layer of security by employing the SSL/TLS protocol. This layer ensures that your data remains protected during the entire transmission process, adding an additional level of privacy and security to your online activities.
Overall, SSTP is a fantastic option for users who prioritize security, privacy, and the ability to access blocked content. With its stealthy operation, robust encryption, compatibility with various platforms, and reliable connection speeds, SSTP stands as a formidable VPN protocol that helps users fly under the radar and enjoy a secure online experience.
When to use a Stealth VPN
When it comes to protecting your online privacy and security, using a VPN is essential. But in some situations, you might need an extra layer of stealth and anonymity. This is where Stealth VPN comes into play.
A Stealth VPN is a specialized type of VPN that focuses on concealing VPN traffic and making it appear as regular internet traffic. It is designed to bypass censorship, overcome network restrictions, and maintain your online privacy without being detected. So, when should you consider using a Stealth VPN?
1. Restricted regions or countries: If you are living or traveling to a region with heavy internet censorship, a Stealth VPN can be your savior. It helps you bypass government restrictions, allowing you to access blocked websites, social media platforms, and other online content that might be otherwise inaccessible. By encrypting your traffic and making it look like regular web traffic, a Stealth VPN allows you to fly under the radar and access the internet freely.
2. Streaming: Streaming services are increasingly implementing VPN detection systems to prevent users from accessing content outside their designated regions. However, with a Stealth VPN, you can easily bypass these restrictions and unlock a whole world of streaming content. Whether it’s accessing popular streaming services like Netflix, Hulu, or BBC iPlayer, or simply wanting to watch your favorite shows while traveling, a Stealth VPN can help you stream without any interruption.
3. Avoiding throttling: Internet service providers (ISPs) often throttle or slow down certain types of internet traffic, such as video streaming or torrenting. By using a Stealth VPN, you can mask your online activities and avoid this throttling. With its ability to disguise VPN traffic as regular web traffic, a Stealth VPN keeps your connection speed consistent and ensures that your ISP cannot discriminate against certain types of data.
4. Enhanced online gaming: Gamers often encounter issues like DDoS attacks, IP bans, or region-specific restrictions while playing online games. By using a Stealth VPN, you can protect yourself from these online threats and access game servers regardless of your location. With the added layer of anonymity and security, a Stealth VPN ensures that your gaming experience remains uninterrupted and safe.
5. Public Wi-Fi security: Public Wi-Fi networks are notorious for their lack of security. Hackers and cybercriminals often lurk on these networks, ready to steal your sensitive information. Using a Stealth VPN on public Wi-Fi encrypts your data and adds an extra layer of security. It prevents anyone on the same network from intercepting your communication and protects your personal information from falling into the wrong hands.
In conclusion, a Stealth VPN is an excellent tool for those looking to enhance their online privacy, bypass restrictions, and protect their sensitive data. Whether you’re in a region with heavy censorship, want to stream geo-blocked content, need to avoid throttling, enhance your gaming experience, or secure your connection on public Wi-Fi, a Stealth VPN can provide the stealth and anonymity you need to fly under the radar. So, don’t compromise on your online privacy – choose a Stealth VPN and take control of your internet experience.
At School/University/Work (hide your VPN usage)
At School/University/Work (Hide Your VPN Usage)
When it comes to using a VPN at school, university, or work, there are times when you may need to hide your VPN usage to ensure your online activities remain private and undetected. While it’s important to respect the rules and policies set by these institutions, there may be legitimate reasons why you want to use a VPN discreetly. Here are some techniques to help you fly under the radar and maintain your online privacy:
1. Use Stealth VPN Protocols: Many VPN service providers offer stealth VPN protocols specifically designed to disguise VPN traffic as regular web traffic. These protocols, such as OpenVPN with TCP port 443 or WireGuard, make it difficult for network administrators to detect VPN usage. By selecting these protocols in your VPN settings, you can circumvent any potential detection mechanisms.
2. Enable Obfuscated Servers: Some VPN providers offer obfuscated servers that further obscure your VPN usage. These servers use advanced encryption and masking techniques to make it nearly impossible for anyone to identify that you are using a VPN. By connecting to an obfuscated server, you can enjoy the benefits of a VPN while avoiding any unwanted attention from network administrators.
3. Use Split Tunneling: Split tunneling is a feature offered by certain VPN providers that allows you to choose which apps or websites you want to route through the VPN and which you want to access directly. By only routing specific traffic through the VPN, you can minimize the chances of your VPN usage being detected. This can be particularly useful if you only need to use a VPN for certain activities like accessing blocked websites or streaming content.
4. Avoid Suspicious VPN Usage Patterns: To avoid arousing suspicion, it’s important to be mindful of your VPN usage patterns. For example, if everyone else at your institution is using the internet normally, it may be suspicious if you suddenly start accessing websites or services that are typically blocked. Try to blend in with the general internet activity around you to avoid drawing attention to your VPN usage.
5. Use Browser Extensions: Some VPN providers offer browser extensions that allow you to encrypt your browser traffic without the need for a full VPN connection. These extensions often come with features like HTTPS encryption and IP masking, which can be useful for maintaining online privacy while browsing. Since they only encrypt browser traffic, they may be less likely to be detected by network administrators.
It’s important to note that while these techniques can help hide your VPN usage to a certain extent, there are no guarantees. Network administrators and IT departments are constantly evolving their detection methods, so it’s essential to familiarize yourself with the rules and policies of your institution to avoid any potential consequences. Now, armed with these tricks, you can enjoy the benefits of a VPN while keeping your online activities private and secure.
To Prevent VPN Throttling
To prevent VPN throttling, there are a few key strategies you can implement to ensure your internet connection remains fast and consistent. VPN throttling occurs when your Internet Service Provider (ISP) intentionally slows down your connection while using a VPN. This can be frustrating, especially when trying to stream content or engage in online activities that require a fast connection. Here are some techniques to help you prevent VPN throttling and maintain optimal speeds:
1. Choose a VPN with server optimization: Some VPN providers offer servers specifically optimized for streaming or P2P activities. These servers are designed to bypass throttling measures implemented by ISPs, allowing you to enjoy faster speeds. Before subscribing to a VPN service, check if they offer server optimization for the activities you primarily engage in.
2. Use servers closer to your location: Connecting to a VPN server closer to your physical location can often result in faster speeds. Lower latency and shorter distances between your device and the VPN server can help prevent throttling. VPN providers usually have a variety of server locations to choose from, so opt for a server that is geographically close to you.
3. Enable VPN protocols with obfuscation: VPN protocols with obfuscation, such as OpenVPN with TCP port 443 or WireGuard, can help mask your VPN usage and make it difficult for ISPs to detect and throttle your connection. These protocols disguise VPN traffic as regular web traffic, making it less likely for your ISP to interfere with your connection.
4. Use a VPN with strong encryption: While encryption is essential for online security, some VPN encryption protocols can be resource-intensive and slow down your connection. Opt for VPN providers that offer strong encryption, such as AES 256-bit, which strikes a balance between security and speed. Strong encryption ensures your data remains secure while minimizing the chances of throttling.
5. Enable split tunneling: Split tunneling is a feature offered by certain VPN providers that allows you to route only specific traffic through the VPN while allowing other traffic to bypass the VPN connection. By selectively routing traffic, you can prevent unnecessary throttling for activities that don’t require VPN protection. This can help maintain faster speeds for non-sensitive browsing or streaming.
6. Use a reputable VPN provider: Choosing a reliable and reputable VPN provider is crucial in preventing VPN throttling. Some VPN services may be more prone to throttling due to their infrastructure or network management practices. Look for VPN providers that have a robust network infrastructure, high-speed servers, and a track record of providing consistent speeds.
By implementing these strategies, you can significantly reduce the likelihood of experiencing VPN throttling and enjoy a fast and unrestricted internet connection. Remember to regularly test your connection speeds and troubleshoot if you notice any significant drops in performance.
For Extra Privacy
When it comes to online privacy, many people are looking for ways to take their security to the next level. While using a VPN is already a great step in protecting your online activity, there are additional measures you can take for extra privacy.
One way to enhance your privacy is by using VPN stealth mode. This feature, offered by certain VPN providers, allows you to fly under the radar and stay hidden from prying eyes. VPN stealth mode works by disguising your VPN usage and making it difficult for anyone to detect that you are using a VPN.
By using VPN stealth mode, you can bypass strict censorship measures implemented by governments or organizations. In countries where internet freedom is restricted, VPN stealth mode can be a game-changer. It allows you to access blocked websites and services without raising suspicion.
Moreover, VPN stealth mode can also help you overcome VPN blocking. Some networks or ISPs actively try to identify and block VPN traffic, making it impossible to use a VPN. However, with VPN stealth mode, your VPN traffic is disguised as regular web traffic, making it harder for any blocks or restrictions to be imposed.
One of the best ways to utilize VPN stealth mode is by using obfuscated servers. These servers are designed specifically to bypass VPN blocking and encryption detection systems. When you connect to an obfuscated server, your VPN connection is masked, making it nearly impossible for anyone to identify that you are using a VPN.
In addition to obfuscated servers, another option for extra privacy is using VPN connections that support multiple VPN protocols. These protocols use advanced encryption techniques and ensure that your traffic is thoroughly encrypted, making it highly secure and difficult to intercept.
Overall, VPN stealth mode is a powerful tool for those who want to take their online privacy to the next level. By disguising your VPN usage and ensuring that your connections are hidden from prying eyes, you can browse the internet with peace of mind, knowing that your online activity is protected. Whether you are accessing blocked websites, evading censorship, or simply safeguarding your sensitive information, VPN stealth mode is an essential feature that provides an extra layer of privacy. So, if you’re concerned about your online security, consider opting for a VPN provider that offers stealth mode and take control of your digital privacy today.
The Best Stealth VPNs in 2020
In today’s digital world, privacy and online security are of utmost importance. With the rise of surveillance and data breaches, it’s crucial to find ways to protect your online activities. One powerful tool that can help you accomplish this is a VPN with stealth mode.
Stealth VPNs are specifically designed to fly under the radar and keep your online activities hidden from prying eyes. They use advanced techniques to disguise your VPN usage, making it nearly impossible for anyone to detect that you’re using a VPN.
If you’re in search of the best stealth VPN in 2020, look no further. We’ve compiled a list of top providers that offer exceptional stealth features to ensure your online privacy:
1. ExpressVPN: Known for its lightning-fast speeds and robust encryption, ExpressVPN offers a stealth mode that allows you to bypass strict censorship measures. With their obfuscated servers, your VPN traffic is disguised as regular web traffic, ensuring maximum privacy.
2. NordVPN: NordVPN is renowned for its extensive server network and top-notch privacy features. Their specialized stealth servers help you bypass VPN blocking and access restricted content effortlessly. With the added benefit of double VPN encryption, your online activities remain hidden and encrypted.
3. Surfshark: With an emphasis on user privacy, Surfshark offers a stealth mode that masks your VPN traffic, making it indistinguishable from regular web traffic. Their Camouflage Mode provides an extra layer of security, allowing you to access restricted content without raising suspicion.
4. CyberGhost: CyberGhost is a fantastic option for users looking for a VPN with advanced privacy features. Their stealth mode ensures that your VPN usage remains hidden from ISPs and other prying eyes. With a strict no-logs policy and high-speed servers, you can browse the internet with peace of mind.
5. Private Internet Access: As the name suggests, Private Internet Access (PIA) is dedicated to safeguarding your online privacy. Their VPN protocol, including OpenVPN and WireGuard, ensures a high level of security. PIA’s stealth mode allows you to bypass VPN detection and access geo-restricted content effortlessly.
When choosing a stealth VPN, it’s essential to consider factors such as server locations, encryption methods, privacy policies, and connection speeds. Additionally, look for providers that offer a user-friendly interface, excellent customer support, and compatibility across multiple devices.
In conclusion, protecting your online privacy is crucial in today’s digital landscape. By using a stealth VPN in 2020, you can fly under the radar and keep your online activities hidden from prying eyes. Consider the top providers mentioned above to ensure maximum privacy and security while browsing the internet.
1. NordVPN
When it comes to stealth VPNs, NordVPN is undoubtedly a top contender. This well-known provider is not only recognized for its vast server network but also for its exceptional stealth features that guarantee your online privacy.
One of NordVPN’s standout features is its specialized stealth servers. These servers are specifically optimized to bypass VPN blocking and provide access to restricted content effortlessly. By disguising your VPN traffic as regular web traffic, NordVPN ensures that no one can detect or intercept your online activities.
Additionally, NordVPN offers an added layer of security with its double VPN encryption feature. With this feature enabled, your internet connection is encrypted twice, providing an extra level of protection for your data. This robust encryption ensures that even if someone manages to detect your VPN usage, they won’t be able to decipher your online activities.
In terms of privacy, NordVPN follows a strict no-logs policy. This means that they do not collect or store any information about your online activities, ensuring your browsing history remains completely anonymous. Their commitment to privacy is further reinforced by their jurisdiction in Panama, which has no mandatory data retention laws.
In terms of server speed, NordVPN doesn’t disappoint either. With their high-speed servers located in various locations around the world, you can enjoy fast and reliable connections for streaming, downloading, and browsing without any frustrating lag or buffering.
What sets NordVPN apart is its user-friendly interface and compatibility across multiple devices. Whether you’re using Windows, macOS, Linux, iOS, Android, or even certain routers, NordVPN has got you covered. Their intuitive apps make it easy to connect to their network and enable the stealth mode, ensuring that your privacy is preserved with just a few clicks.
Lastly, NordVPN offers excellent customer support, with 24/7 live chat assistance available. If you run into any issues or have any questions about their stealth features or any other aspect of their service, their knowledgeable support team is ready to assist you.
In conclusion, NordVPN is a reliable and trustworthy choice for those seeking a stealth VPN. With their specialized stealth servers, double VPN encryption, strict no-logs policy, and excellent server speeds, NordVPN ensures your online privacy and security are never compromised. Whether you want to access geo-restricted content or simply keep your online activities hidden, NordVPN has the advanced features and robust infrastructure to meet your needs.
2. VyprVPN
When it comes to VPN services, VyprVPN is a name that stands out for its commitment to providing top-notch security and privacy. One of the key features of VyprVPN is its ability to offer “Chameleon” protocol, which is specifically designed to bypass VPN blocking and censorship. This protocol uses advanced encryption techniques to mask VPN traffic, so you can fly under the radar and access restricted websites and services with ease.
VyprVPN also takes privacy seriously with its no-logs policy. They do not collect or store any information about your online activities, ensuring that your browsing history remains completely private and anonymous. In addition, VyprVPN operates its own network of servers, providing an extra layer of security and privacy compared to VPN providers that rely on third-party servers.
When it comes to server speed, VyprVPN doesn’t disappoint either. They have a global network of high-speed servers strategically located in various locations around the world, ensuring fast and reliable connections. Whether you’re streaming your favorite shows, downloading large files, or simply browsing the web, VyprVPN delivers consistent speeds to enhance your online experience.
Furthermore, VyprVPN offers user-friendly apps for a wide range of devices, including Windows, Mac, iOS, and Android. With their easy-to-use interface, connecting to their network and enabling the stealth mode is a breeze. Whether you’re at home, in the office, or on the go, you can protect your online privacy and security with just a few clicks.
Another standout feature of VyprVPN is its proprietary technology, called the VyprDNS. This technology ensures that your DNS requests are encrypted and anonymized, preventing any leaks or vulnerabilities. With VyprDNS, you can have peace of mind knowing that your online activities are secure and protected from prying eyes.
In terms of customer support, VyprVPN offers a reliable and responsive team ready to assist you. Whether you have technical questions, need help troubleshooting, or simply want to inquire about their stealth features, their knowledgeable support staff is available 24/7 to provide assistance via live chat or email.
In conclusion, VyprVPN is a fantastic option for anyone looking to enhance their online security and privacy. With its advanced features like the Chameleon protocol, no-logs policy, high-speed servers, and user-friendly interface, VyprVPN goes the extra mile to ensure that your online activities remain private and protected. Whether you’re a casual internet user or a business professional, VyprVPN is a trusted VPN provider that delivers reliable and robust protection for your online security.
3. Torguard
3. Torguard: Unleashing Stealth Mode for Ultimate Privacy
When it comes to online privacy and anonymity, Torguard is a name that stands out. With its advanced features and robust encryption, Torguard empowers users to fly under the radar and enjoy a truly private internet experience.
One of the key highlights of Torguard is its Stealth VPN technology. This feature allows users to bypass VPN detection and censorship, making it an ideal choice for individuals living in countries with strict internet regulations. By disguising VPN traffic as regular HTTPS traffic, Torguard ensures that your online activities remain hidden from prying eyes.
Torguard also provides an impressive network of servers across the globe. With over 3,000 servers in more than 55 countries, users can enjoy excellent speeds and reliable connections from anywhere in the world. Whether you’re streaming your favorite shows on popular services like Netflix or BBC iPlayer, or simply browsing the web, Torguard ensures faster speeds and seamless performance.
In addition to its exceptional privacy features, Torguard offers a strict no-logs policy. This means that they do not record or store any information about your online activities, ensuring that your browsing history remains completely private. With Torguard, you can have peace of mind knowing that your online footprint is erased, leaving no trace for anyone to follow.
Torguard goes the extra mile when it comes to security. In addition to its robust encryption, Torguard offers an array of advanced security features such as DNS leak protection and an ad-blocker. These features further enhance your online security and protect you from potential vulnerabilities or data leaks.
For those who value convenience and flexibility, Torguard provides a range of user-friendly apps and browser extensions. Whether you’re using Windows, Mac, iOS, Android, or even Chrome or Firefox, Torguard has got you covered. Connecting to their network and activating stealth mode is a breeze with their intuitive and easy-to-use interface.
Customer support is another area where Torguard excels. With a dedicated team available 24/7, you can rely on their prompt assistance whenever you need it. Whether you have technical inquiries or need help troubleshooting, Torguard’s knowledgeable support staff is just a click away, ready to address any concerns or questions.
In conclusion, Torguard brings a fantastic option for those seeking ultimate online privacy and security. With its stealth mode, extensive server network, strict no-logs policy, and advanced security features, Torguard ensures that your online activities fly under the radar while delivering fast and consistent speeds. Trust Torguard to safeguard your privacy and browse the internet with peace of mind.
4. IPVanish
When it comes to online security and privacy, IPVanish is a top choice among VPN services. With its impressive range of features and commitment to user anonymity, IPVanish allows you to browse the web with complete peace of mind.
One of the standout features of IPVanish is its multi-platform compatibility. Whether you’re using Windows, macOS, iOS, Android, or even Fire TV, IPVanish has dedicated apps that are easy to install and use. This makes it a convenient option for users across various devices.
IPVanish also offers a generous allowance of simultaneous connections. With a single subscription, you can protect up to 10 devices simultaneously, allowing you to secure your entire household’s online activities without any additional costs. This is especially advantageous for families or individuals who own multiple devices.
When it comes to speed, IPVanish delivers excellent performance. With high-speed servers strategically located in over 75 countries, users can experience faster speeds and seamless streaming. Whether you’re downloading large files, streaming content on popular platforms like Netflix or BBC iPlayer, or engaging in online gaming, IPVanish ensures that you won’t be slowed down.
In terms of security, IPVanish offers robust encryption with AES 256-bit. This ensures that your online activities and personal information are shielded from potential hackers or surveillance. IPVanish also has a strict no-logs policy, meaning they do not collect or store any information about your browsing habits. This commitment to privacy ensures that your online footprint remains completely secure and private.
IPVanish takes further steps to protect your online security with features like DNS leak protection and a kill switch. The DNS leak protection feature prevents your DNS requests from being leaked, while the kill switch automatically disconnects your internet connection if the VPN connection drops, ensuring that your data is always protected.
Customer support is another area where IPVanish excels. Their dedicated support team is available 24/7 via live chat and email, ready to assist you with any technical inquiries or troubleshooting. Whether you’re a beginner or an experienced user, you can rely on IPVanish’s knowledgeable staff to provide prompt and efficient assistance.
In conclusion, IPVanish offers a comprehensive VPN service with advanced security features, excellent speed, and a user-friendly interface. Whether you’re concerned about online privacy or want to bypass geo-restrictions to access your favorite content, IPVanish is a fantastic option that ticks all the boxes.
5. Other VPNs
While IPVanish is a top-notch VPN provider, there are also other VPNs that offer unique features and excellent performance. Here are five other VPNs that you should consider:
1. ExpressVPN: Known for its lightning-fast speeds and extensive server network, ExpressVPN is a fantastic option for anyone looking to stream content or engage in online gaming. With servers in over 94 countries, you can access popular streaming services like Netflix and Hulu from anywhere in the world. ExpressVPN also offers a 30-day money-back guarantee, giving you plenty of time to test out their service.
2. NordVPN: With advanced features like double encryption and obfuscated servers, NordVPN offers an extra layer of security for those who require utmost privacy. Their strict no-logs policy ensures that your online activity is never recorded. NordVPN also provides high-speed servers and unlimited bandwidth, making it an excellent choice for downloading large files or streaming content seamlessly.
3. CyberGhost: If you’re new to VPNs and want a user-friendly experience, CyberGhost is a fantastic option. Their intuitive interface and easy setup make it a great choice for beginners. CyberGhost also has an impressive server network, with over 7,000 servers in 90 countries. They offer dedicated apps for all major platforms and have a 45-day money-back guarantee, so you can test their service risk-free.
4. Surfshark: Despite being a relatively new player in the VPN market, Surfshark has quickly gained popularity due to its privacy features and affordability. With unlimited simultaneous connections, you can protect all your devices with a single subscription. Surfshark also offers a wide range of server locations and has a strict no-logs policy, ensuring that your online activity remains completely private.
5. Private Internet Access (PIA): If online privacy is your top priority, Private Internet Access is worth considering. They have a robust no-logs policy and provide industry-standard encryption to protect your data. PIA also offers a wide range of advanced features, including ad and malware blockers, as well as SOCKS5 proxy access. With servers in over 78 countries, PIA provides excellent speeds and reliable performance.
Each of these VPN providers offers unique features and a high level of security. Whether you’re looking for advanced encryption, unlimited simultaneous connections, or a user-friendly experience, you can find a VPN that suits your needs. Consider these options carefully and choose the one that offers the best combination of features and performance for your online privacy and security.

Leave a Reply